The MITRE EMB3D™ Threat Model
The EMB3D Threat Model provides a cultivated knowledge base of cyber threats to embedded devices, providing a common understanding of these threats with security mechanisms to mitigate them.
What's New
- Apr. 29, 2025: Minor bug fix release v2.0.1.
- Apr. 22, 2025: MITRE released EMB3D version 2.0. The release includes a JSON-based STIX representation of the model to support tool integration, new Properties (PID-28 / 34 / 33), Threats (TID-225 / 226), and Mitigations (MID-84, 85, 86, 87, 88, 89). The release also includes expanded definitions, references, and numerous technical edits. See the Changelog here.
- Feb. 27, 2025: MITRE and Red Balloon Security hosted a public webinar that introduces the EMB3D framework and provides case studies on how EMB3D can be used to evaluate device security by mapping its properties to potential threats. Watch the video here.
- Jan. 17, 2025: Learn how to use EMB3D with STRIDE for better threat modeling over on our new blog.
What is EMB3D™
EMB3D is a threat model for embedded devices found in industries such as critical infrastructure, Internet of Things, automotive, healthcare, manufacturing, and many more. The threat model is intended to be a resource to help vendors, asset owners/operators, test organizations, and security researchers to improve the overall security of embedded devices' hardware and software. This threat model aims to serve as a central repository of information, defining known threats to embedded devices and their unique device features/properties that enable specific threat actions. By mapping the threats to the associated device features/properties, the user can easily enumerate threat exposure based on the known device features.
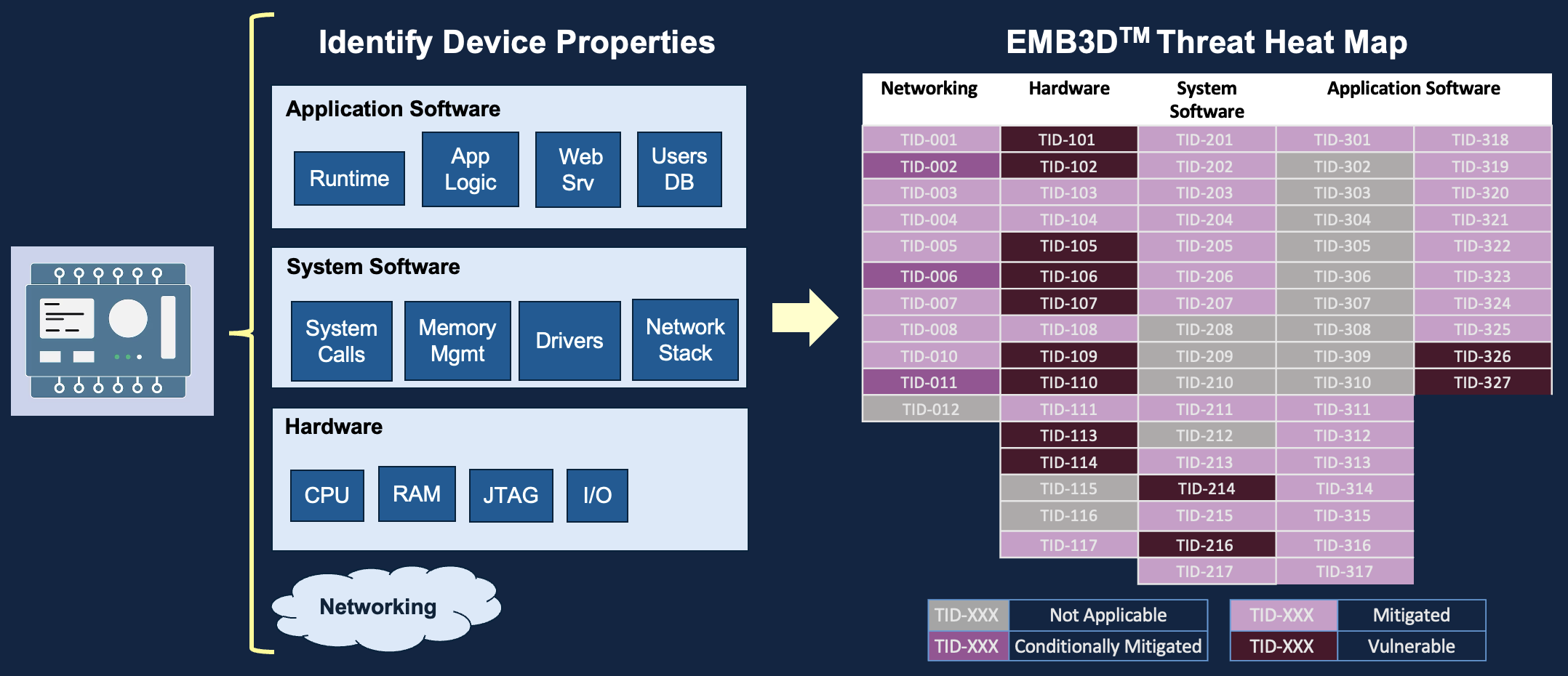
Device Properties
Device properties describe a device's hardware and software components and capabilities of a device. These include physical hardware, network services and protocols, software, and firmware. Each category is further divided into sub-properties that are then mapped to a set of threats. By mapping properties, users can identify the threats associated with a given device property.
Threats
EMB3D threats identify how a threat actor can achieve a specific objective or effect on a system or device. Each threat description includes (i) information about the technical features that are targeted by the threat; (ii) the actions that must be performed by the threat actor to cause the threat's effect, including the impact or effect the threat will have on the device; and (iii) the vulnerabilities or weaknesses within that mechanism that enable the threat actions.
Mitigations
Mitigation strategies and techniques are described for each threat. These can be leveraged by device vendors to prevent and reduce the risk of a threat, and by end users to validate that devices are sufficiently protected against that threat. The mitigations define the mechanisms or technologies that protect against the threat while remaining flexible in how mitigations can be implemented within the device's unique constraints.
EMB3D Users
Device Vendors
Support device threat models and provide guidelines for mitigations requirements/designs. Develop device roadmaps for evaluating device risk and prioritizing mitigation efforts.
Asset Owners & Operators
Inform acquisition requirements and decisions about unmitigated threats/risks. Support acquisition efforts related to evaluating a device's security capabilities. Guide the development and deployment of compensating controls around unmitigated threats.
Security Researchers/Testers
Scope assessment activities and outcomes. Help identify potential trouble spots for deeper investigation. Contribute to research efforts around novel threats and mitigations.