Applying EMB3D™
Step 1. Enumerate device properties and map to threats
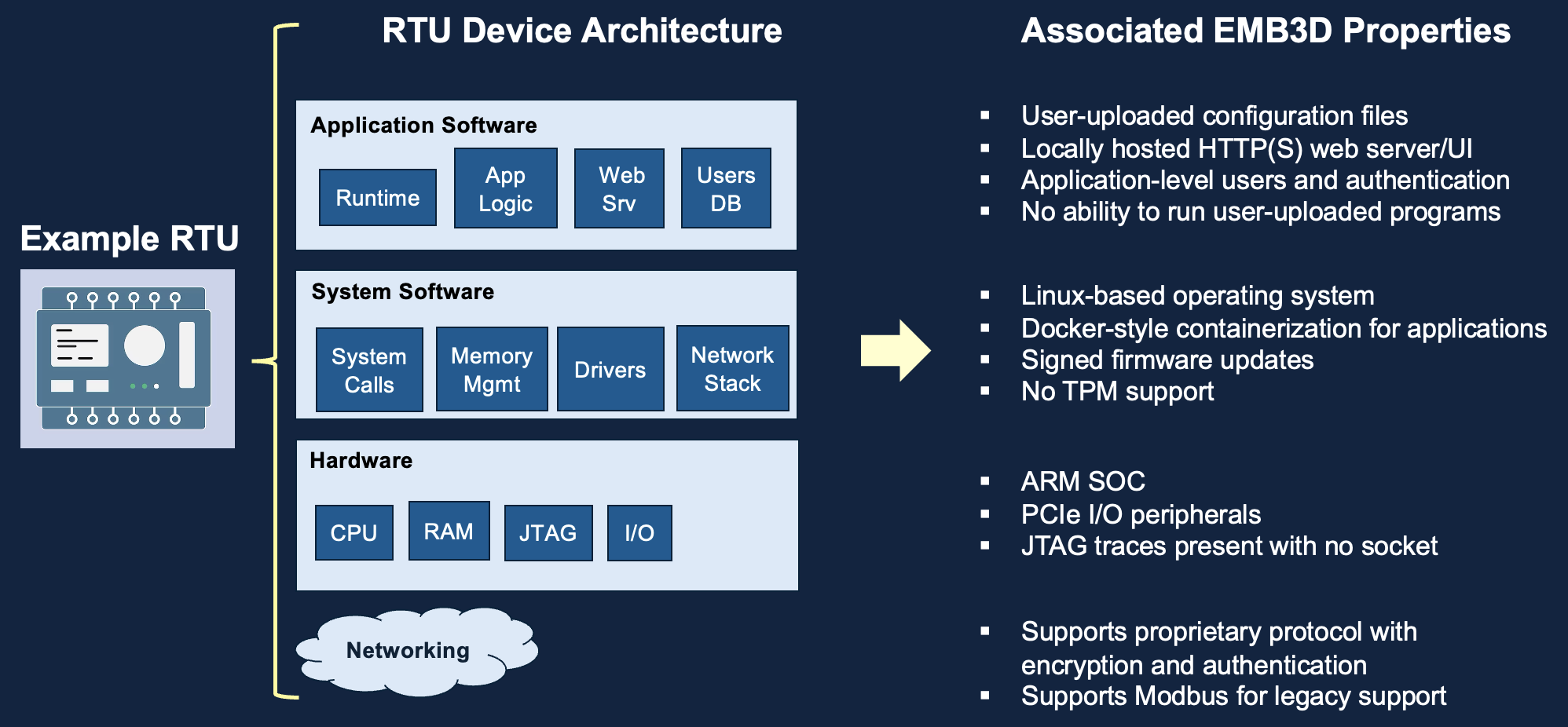
First, identify the set of Device Properties List that apply to the device being evaluated based on device knowledge and documentation. While a vendor may be able to fully enumerate all properties, an asset operator or security researcher may need to review available documentation or perform initial device testing or decomposition to fully enumerate the relevant properties.
Select the applicable properties in the Properties Mapper Tool to generate the list of Threats the device may be exposed to because it incorporates those properties and features.
Properties to Threats MapperStep 2. Enumerate threats and evaluate their relevance/risk
After identifying the device’s properties list and obtaining the candidate threat mapping, the next step is to review each potential threat to determine if it truly applies to the device and how much risk it poses. For additional details, follow the threat detail links output by the Mapper Tool or look up the associated Threat ID (TID) in the Threats catalog. Each threat description provides additional information about that threat, including its maturity level, documented threat evidence and CVEs, and associated weaknesses from the CWE database. This information helps to better understand the mechanics of the threat, its prerequisites, how it manifests on embedded devices, and how threat actors might utilize it, which can be used to better understand the risk of that threat to the device in question.
Step 3. Identify required mitigations
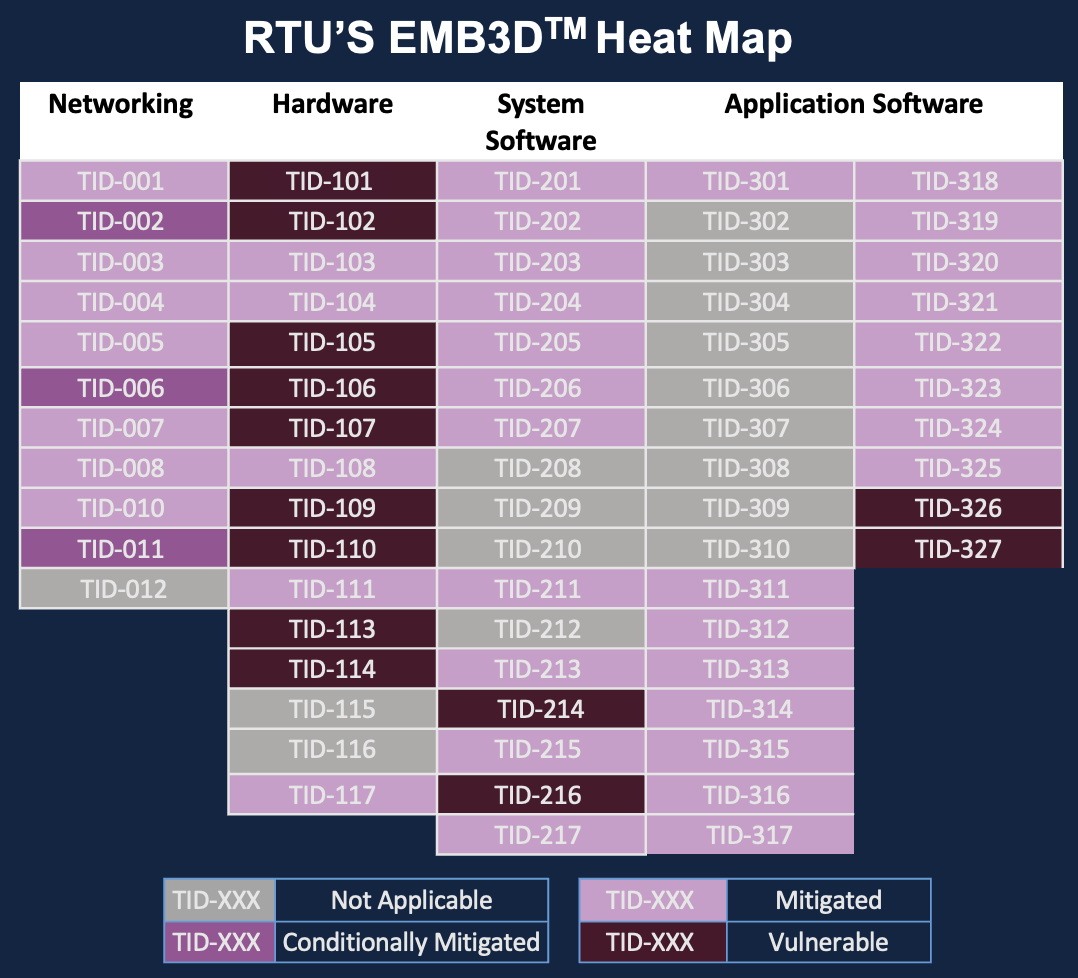
Equipped with a list of threats that pose a viable risk to the device, the next step is to determine if the device sufficiently defends against those threats. Coming in the next release of EMB3D in Summer 2024, each threat description will include a set of Foundational, Intermediate, and Leading mitigations. These mitigations will provide guidance on what technical mechanisms can best prevent or reduce the risk of that threat. Mitigations will include references to guidance documents and best practices, along with information about potential limitations and challenges when deploying each mitigation.
The mitigation recommendations can then be used to make decisions and plans about the device. Device vendors may use the mitigations mapping to prioritize their security engineering efforts and choose technical security mechanisms that will be most effective against current and future threats. Asset owners and operators may use it to inform acquisitions, make judgements about the risks of devices deployed in their environments, or what additional environmental-level mitigations they wish to make to address residual risk. Finally, security researchers can use this information to organize and triage their efforts to determine which aspects of a device are worth deeper investigation.